Day-7:Deep Dive into Security Groups and NACL in AWS
Let’s start with the basic definitions
Security Group — Security Group is a stateful firewall to the instances. Here stateful means, security group keeps a track of the State. Operates at the instance level.
Network Access Control List — NACL is stateless, it won’t keep any track of the state. Operates at Subnet level.

Security Group:
Security Group is a stateful firewall which can be associated with Instances. Security Group acts like a Firewall to Instance or Instances. Security Group will always have a hidden Implicit Deny in both Inbound and Outbound Rules. So we can only allow something explicitly, but not deny something explicitly in Security Groups.
Default Security Group:
By default a Security Group is like:
In Security Group, there are two things to discuss — AWS created Default SG, User Created Default SG.
AWS creates a default SG when it creates a default VPC — in this security group they will add an inbound rule which says all Instances in this Security Group can talk to each other.
Any Security Group created by a User explicitly, wouldn’t contain this Inbound Rule which would allow communication between the Instances, we should explicitly add it if required.
Both in the AWS created SG and User Created Custom SG , the Outbound Rules would be the same — which allows ALL TRAFFIC out.
We cannot add a Deny Rule, both in Inbound and Outbound Rules as there’s a hidden default Implicit Deny Rule in Security Groups. All we can do is allow which is required, everything else which isn’t allowed by us is blocked.
A default security group that is created by default in the default VPC by AWS looks like this —
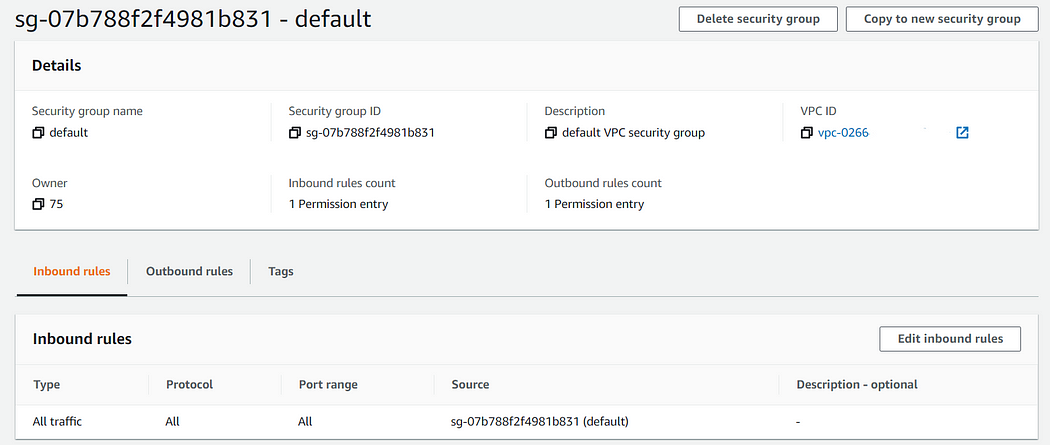

Security Group Features:
There are two main features which will make Security Groups different from NACLs —
Stateful Firewall
Connection Tracking
Stateful Firewall:
Stateful means — maintain the state of connection so that you introduce yourself only once, not every time you start talking — think TCP session, once established, they start talking till one of them says Finish or Reset.
The reason why a Security Group is called a Stateful Firewall is — Security Group basically maintains the State of a connection, meaning — if an instance sends a request , the response traffic from outside is allowed back irrespective of the inbound rules, and vice versa.
Example: If my security group inbound rule allows NO TRAFFIC and outbound rule allows ALL TRAFFIC and I visit a website on my instance, the response from the WebServer back to my instance will be allowed even though the inbound rule denies everything.
Security Group achieves this by leveraging something knows as Connection Tracking which we will be discussing shortly.
Connection Tracking:
Security Groups use Connection Tracking to keep track of connection information that flows in and out of an instance, this information includes — IP address, Port number and some other information(for some specific protocols).
Security Group needs to track any connection only in this case — if there’s no inbound/outbound rule that allows everything. Let’s say we have allowed ALL traffic from outside and ALL traffic to outside, it need not track anything because, whatever comes and goes should be allowed.
Security Group Rule Fields:

Type — Type of Traffic which can be TCP, UDP, ICMP. Type field provides the well-used protocols, when selected it auto fills the Protocol field. You may also select a Custom Protocol Rule, which allows you to select the Protocol field from a wide range of Protocols.
Protocol — As mentioned already, if you select a Custom Protocol Rule in Type field, you can select a Protocol from the available Protocol List.
Port Range — You can specify a single port or a range of ports like this 5000–6000.
Source[Inbound Rules only] — Can be Custom — a single IP address or an entire CIDR block, Anywhere — 0.0.0.0/0 in case of IPv4, My IP Address — AWS auto-detects your Public IP address. Destination can only be mentioned in Outbound Rule.
Destination[Outbound Rules only] — Can be Custom — a single IP address or an entire CIDR block, Anywhere — 0.0.0.0/0 in case of IPv4, My IP Address — AWS auto-detects your Public IP address. Source can only be mentioned in Inbound Rule.
Description — This field is optional. You can add a description which helps you to keep a track of which rule is for what.
NACL — Network Access Control List:
NACLs are stateless firewalls which work at Subnet Level, meaning NACLs act like a Firewall to an entire subnet or subnets. A default NACL allows everything both Inbound and Outbound Traffic. Unlike Security Groups, in NACLs we have to explicitly tell what to deny in Inbound and Outbound Rules. There’s no Implicit Deny in NACL.
Default NACL:
By default a NACL is like:
When we create a VPC, a default NACL will be created which will allow ALL Inbound Traffic and Outbound Traffic. If we don’t associate a Subnet to NACL, the default NACL in that VPC will be associated to that Subnet. A default NACL looks like this —


NACL Features:
Statelessness:
Unlike Security Groups, NACL doesn’t maintain any track of connections which makes it completely Stateless, meaning — if some traffic is allowed in NACL Inbound Rule, the response Outbound traffic is not allowed by default unless specified in the Outbound Rules.
NACL Rule Fields:


Rule Number — Rules are evaluated starting with the lowest numbered rule. If a rule matches, it gets executed without checking for any other higher numbered rules.
Type — Type of Traffic which can be TCP, UDP, ICMP. Type field provides the well-used protocols, when selected it auto fills the Protocol field. You may also select a Custom Protocol Rule, which allows you to select the Protocol field from a wide range of Protocols.
Protocol — As mentioned already, if you select a Custom Protocol Rule in Type field, you can select a Protocol from the available Protocol List.
Port Range — You can specify a single port or a range of ports like this 5000–6000.
Source[Inbound Rules only] — Can be a Single IP Address or an entire CIDR block. Destination can only be mentioned in Outbound Rule.
Destination[Outbound Rules only] — Can be a Single IP Address or an entire CIDR block. Source can only be mentioned in Inbound Rule.
Allow/Deny — Specifies whether to allow or deny traffic.
Security Group and NACL Key Differences:
The differences between NACL and security groups have been discussed below:
| NACL | Security Group |
| Network Access Control List that helps provide a layer of security to the amazon web services. There are two kinds of NACL- Customized and default. | A security group has to be explicitly assigned to an instance; it doesn’t associate itself to a subnet. |
| Multiple subnets can be bound with a single NACL, but one subnet can be bound with a single NACL only, at a time | Security groups are associated with an instance of a service. It can be associated with one or more security groups which has been created by the user. |
| NACL can be understood as the firewall or protection for the subnet. | Security group can be understood as a firewall to protect EC2 instances. |
| These are stateless, meaning any change applied to an incoming rule isn’t automatically applied to an outgoing rule. | These are stateful, which means any changes which are applied to an incoming rule is automatically applied to a rule which is outgoing. |
| Example: If a request comes through port 80, it should be explicitly indicated that its outgoing response would be the same port 80. | Example: If the incoming port of a request is 80, the outgoing response of that request is also 80 (it is opened automatically) by default. |
| NACL can be used to support as well as deny rules. Denial of rules can be explicitly mentioned, so that when the layer sees a specific IP address, it blocks connecting to it. | They support rules only, and the default behaviour is denial of all rules. |
Every VPC can belong to different security groups. | | It is considered to be the second layer of defence, which helps protect AWS stack. It is an optional layer for VPC, which adds another security layer to the amazon service. | It is considered to be the first defence layer that helps protect the Amazon Web Services infrastructure. | | In case of NACL, the rules are applied in the order of their priority, wherein priority is indicated by the number the rule is assigned. | In case of a security group, all the rules are applied to an instance. | | This means every rule is evaluated based on the priority it has. | This means all rules are evaluated before they allow a traffic. |
Use Case:
I will give an example to make you understand when to use Security Group and when to use NACL —
Let’s say you have allowed SSH Access of an Instance to a User in Dev Team and he’s connected to it and actively accessing it and for some reason(realizing that the user is involved in some malicious activity) you wanted to remove his SSH access.
In this case you have two choices — 1) Remove SSH inbound allow rule of that user in the Security Group Inbound Rule. 2) Add an NACL Rule explicitly denying traffic from his IP address. If you go with the first one, he would not lose his SSH connection, this is due to the connection tracking behavior of Security Groups. If you go with the latter choice, NACL would immediately block his Connection. So in this case, it’s better to use a NACL Deny Rule rather than deleting a Security Group allow Rule.
